ICE Is Using Phone Extraction Software Linked to Russia’s FSB-Connected Network

Over the past decade, federal agencies have dramatically expanded their use of digital surveillance and extraction tools, embedding mobile forensics software into immigration enforcement, criminal investigations, and national security operations. One of the tools currently used by ICE traces back to a company connected to Russia’s mobile forensics industry — and to an FSB-linked network tied to one of the FBI’s most wanted hackers.
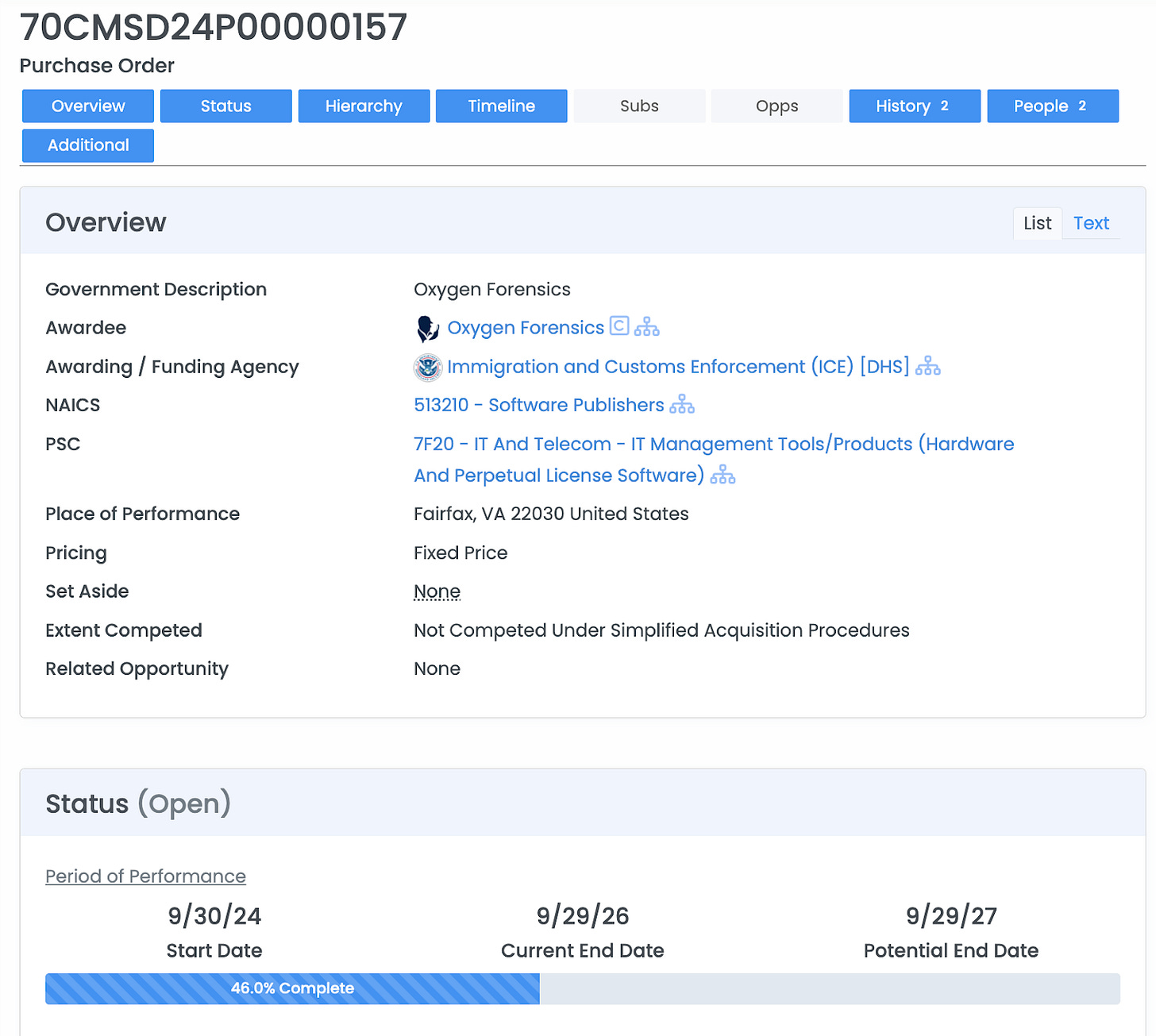
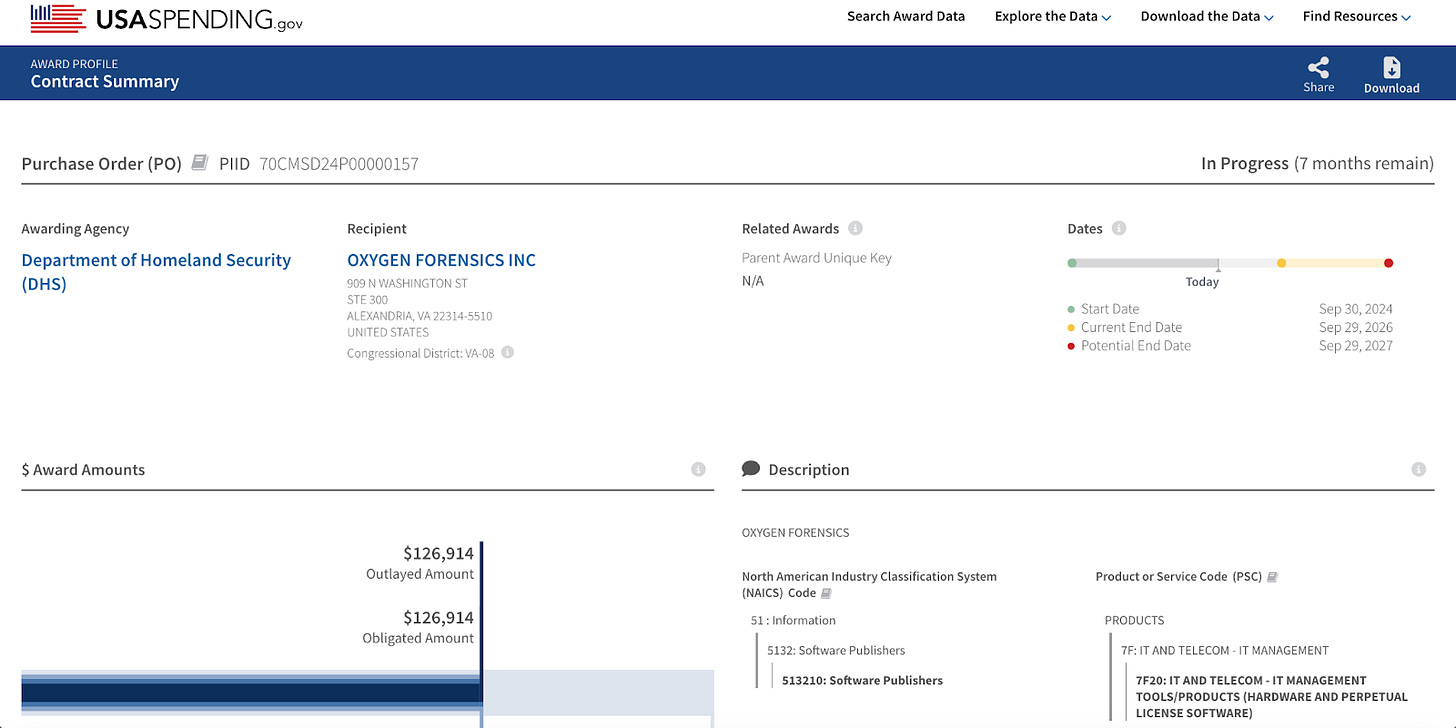
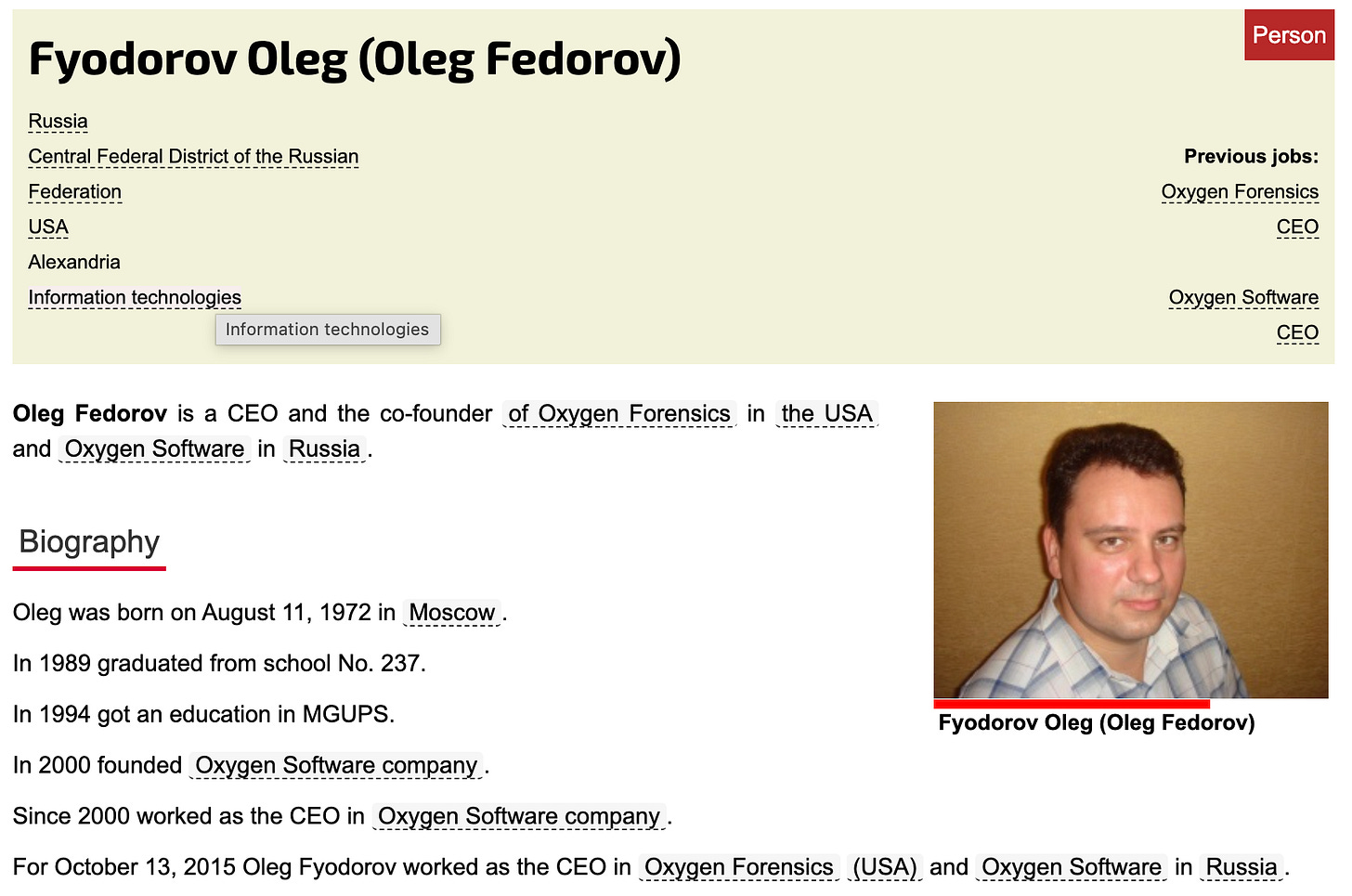
On September 30, 2024, ICE signed another federal contract with Oxygen Forensics Inc., a digital forensics company based in Alexandria, Virginia. The company’s software is designed to extract messages, deleted files, location history, application data, and other information from smartphones and convert it into structured investigative reports. This is the kind of contract that has gone unnoticed — until now.
Last week, Radio Svoboda published a detailed investigation into Eduard Bendersky, a veteran of the FSB’s elite Vympel special forces unit and the father-in-law of FBI-indicted and wanted hacker leader Maksim Yakubets. The reporting examined Bendersky’s expanding role inside Russia’s defense and technology sectors following Russia’s full-scale invasion of Ukraine, including his leadership of a Soviet-era telecommunications institute involved in satellite communications and missile electronics, as well as his investments in cybersecurity and data infrastructure companies operating under FSB licensing.
The investigation also documented how Russian authorities are deploying Mobile Forensic Detective systems at border crossings. Citizens returning to Russia after fleeing the country during the war described being required to hand over their phones for forensic extraction. Officers connected devices to standardized kits capable of recovering deleted messages, geolocation data, cached social media content, browser histories, and encrypted communications. Within hours, the data was indexed, keyword searched, and in some cases used to initiate criminal proceedings tied to anti-war speech or so-called “extremism.”
Mobile Forensic Detective traces back to a company once known as Oxygen Software, later reorganized as MKO Systems. Russian procurement records and court filings show that Mobile Forensic tools have been supplied to agencies, including the FSB and the Ministry of Internal Affairs, and have been used in politically sensitive prosecutions. Separately, in 2021, Oxygen received an FSB license authorizing it to carry out work involving cryptographic technologies.
And that same network connects to a hacker that has been on the FBI’s radar for years...
In December 2019, the FBI indicted Maksim Yakubets, believed to be living in Russia, alleging that he led the Evil Corp cybercriminal organization responsible for global banking malware and ransomware campaigns that stole tens of millions of dollars from financial institutions and corporations worldwide. The United States offered a $5 million reward for information leading to his arrest, one of the largest bounties ever placed on a cybercriminal.
By the time of the indictment, Yakubets had already married into Russia’s security establishment. In 2017, he married the daughter of Eduard Bendersky, a former officer in Vympel, the elite special operations unit within Russia’s Federal Security Service, the successor to the KGB. Vympel is a clandestine unit responsible for counterterrorism, sabotage, assassinations, and other covert operations inside Russia and abroad.

By 2024, coordinated actions by authorities in the United States, the United Kingdom, and Australia led to additional sanctions against members of Evil Corp, known in cybersecurity circles as INDRIK SPIDER. Eduard Bendersky was among those sanctioned. Law enforcement officials stated that he used his influence to connect the ransomware group with Russian intelligence services and helped shield its members after the 2019 U.S. indictments. Officials further assessed that, prior to 2019, Russian intelligence services had tasked INDRIK SPIDER with carrying out cyberattacks and espionage against NATO member states.
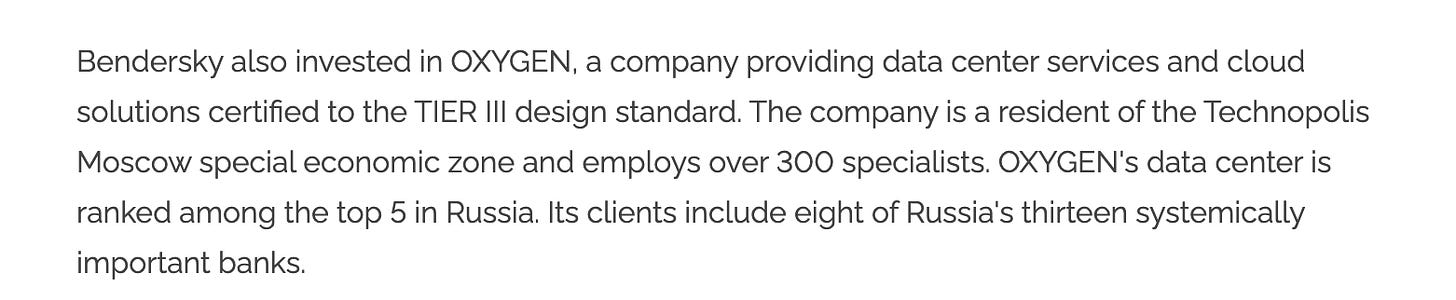
Bendersky’s role extends well beyond his family connection to Yakubets. In the years following the indictment, he emerged as an investor in OXYGEN, a Moscow-based data infrastructure company operating inside a state-linked technology zone, and took on a leadership role at the sanctioned Moscow Research Institute of Radiocommunications — a Soviet-era defense telecommunications institute involved in strategic communications, satellite systems, and aviation electronics within Russia’s military-industrial complex.
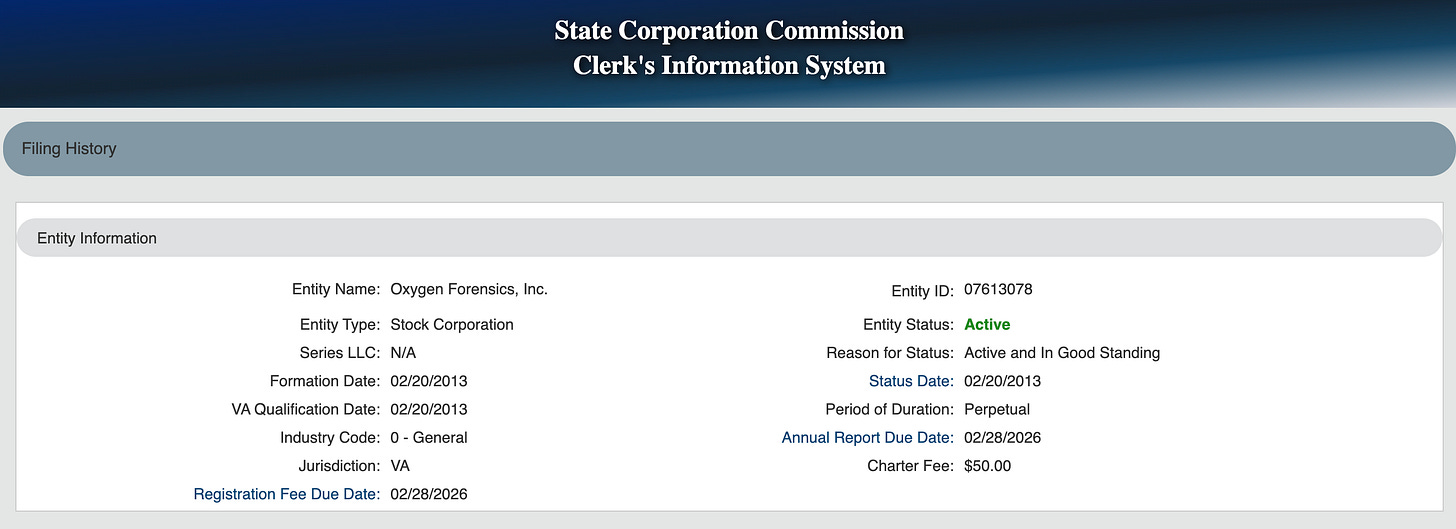
And for over a decade, the Oxygen brand has been operating in both countries. Oxygen Software was founded in Moscow in the early 2000s by Russian developers Oleg Fedorov and Oleg Davydov, and by 2013 expanded into the United States as Oxygen Forensics Inc. The American entity was formally registered in Virginia and began marketing mobile extraction software to U.S. law enforcement agencies.
By the mid-2010s, Oxygen Forensics had secured contracts with the U.S. Secret Service, the FBI, ICE, and other federal agencies, integrating its tools into federal investigative workflows. Meanwhile, Russian business reporting noted that by 2025, Mobile Forensic had become the leading smartphone extraction platform in Russia.
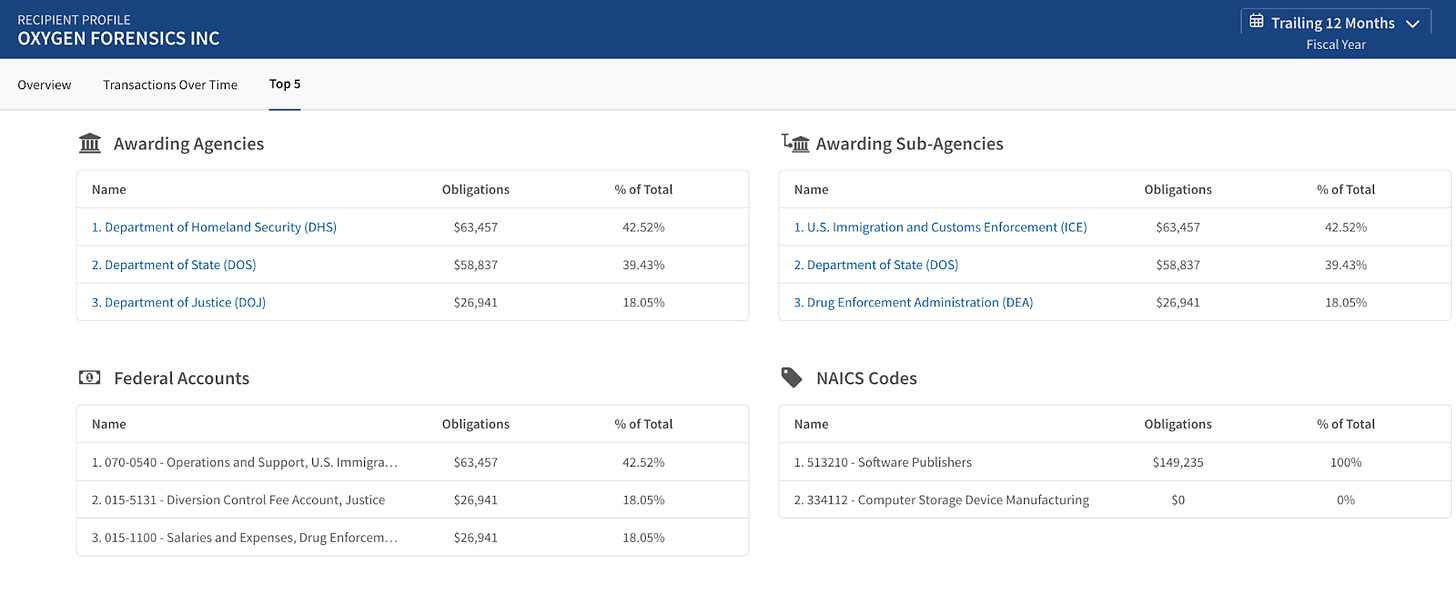
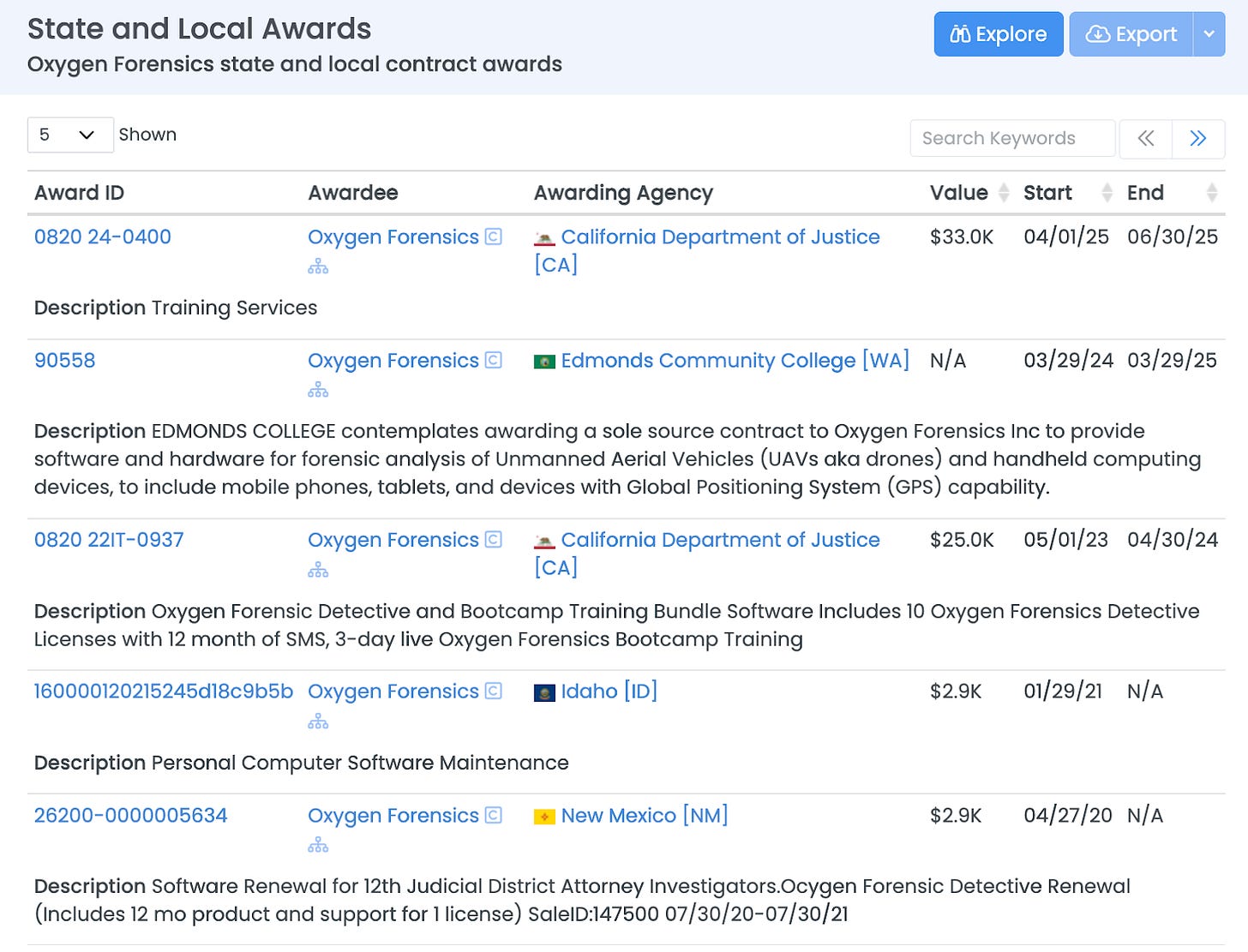
Today, Oxygen Forensics Inc., the U.S.-registered entity, continues to hold contracts with the federal government. Records reflect current and prior awards from ICE, the FBI, the Drug Enforcement Administration, Customs and Border Protection, and the State Department. The company maintains an active federal contractor registration through September 2026 and remains eligible for additional federal awards.
Like its Russian counterpart, Mobile Forensic — emerged from the same origins as Oxygen Software origins — Oxygen Forensic is built to extract and analyze data from smartphones, including Apple iOS devices such as iPhones, and other digital devices used in criminal and national security investigations. The software can recover encrypted or deleted communications, application data, call logs, device metadata, and other digital artifacts, compiling them into structured reports designed for evidentiary use. The capabilities closely resemble those described in Radio Svoboda’s reporting on the systems deployed at Russian border crossings.
The technical relationship between the Russian and American product lines surfaced publicly in late 2023, when the Russian firm Elcomsoft filed suit in Moscow arbitration court alleging that MKO Systems incorporated proprietary code enabling deep extraction from Apple iOS devices, including access to passwords, browsing histories, photographs, and other protected data. Independent reporting in Forbes noted that comparable technical methods appeared in Oxygen Forensic Detective. Although the case ended in a settlement in Russia, the litigation drew attention to the technical proximity between tools supplied to Russian security services and those used by U.S. agencies.
The use of Russian-founded forensic tools within U.S. investigative systems is not new. As early as 2016 and 2017, Oxygen Forensics, Elcomsoft, and other Eastern European digital forensics firms were supplying extraction tools to U.S. federal agencies, even as scrutiny of Russian cyber operations intensified following Russia’s 2016 election interference. ICE had already contracted for Oxygen software in 2016, and the Secret Service entered into six-figure agreements for similar capabilities. During the same period, congressional committees sought information about DHS contracts for electronic device search software, reflecting oversight concerns about vendors operating within sensitive federal systems.
Those concerns unfolded alongside efforts to remove Moscow-based Kaspersky Lab software from federal networks over fears that Kremlin pressure could create hidden access pathways. Kaspersky products were ultimately barred from federal use. Mobile forensic tools developed by Russian-founded companies, however, remained embedded in enforcement environments.
Mobile extraction systems are now central to investigative practice across jurisdictions. In Russia, they are used at border crossings and in cases targeting dissent and political speech. In the United States, they have been used in immigration enforcement, criminal investigations, and national security cases, embedded in procurement cycles and agency budgets, and are now increasingly deployed at border crossings for all visitors and in investigations involving protests and politically sensitive matters.
There is no public evidence of a direct operational alliance between Russian intelligence services and U.S. agencies using Oxygen software. What the record does show is a technology supply chain that crosses geopolitical fault lines. Digital forensic tools with documented Russian corporate origins, historical ties to Moscow’s security-adjacent ecosystem, sanctioned individuals and entities, and parallel product development pathways are operating inside U.S. federal investigative systems.
A company whose technology traces back to Russia’s digital extraction industry — and whose related products have been supplied to agencies including the FSB — is operating inside U.S. immigration and law enforcement systems, even as Russia remains a hostile U.S. adversary. At the same time, ICE’s use of phone data extraction tools is expanding at border crossings, in immigration enforcement actions, and against protesters. Congress needs to examine how these contracts were approved, what safeguards are in place, and why federal agencies are relying on technology linked to an adversary’s security ecosystem.









Why the label adversary? Two fascist(oid) state instituitions using common apps. Business as usual. The White House Alaska photos signs of(f) the deal.
Using ruzzian software should have them all executed for acts of treason without trail. Their all legally spies who are undermining NATO.